Riding the State Unemployment Fraud ‘Wave’
When a reliable method of scamming money out of people, companies or governments becomes widely known, underground forums and chat networks tend to light up with activity as more fraudsters pile on to claim their share. And that’s exactly what appears to be going on right now as multiple U.S. states struggle to combat a tsunami of phony Pandemic Unemployment Assistance (PUA) claims. Meanwhile, a number of U.S. states are possibly making it easier for crooks by leaking their citizens’ personal data from the very websites the unemployment scammers are using to file bogus claims.
Last week, the U.S. Secret Service warned of “massive fraud” against state unemployment insurance programs, noting that false filings from a well-organized Nigerian crime ring could end up costing the states and federal government hundreds of millions of dollars in losses.
Since then, various online crime forums and Telegram chat channels focused on financial fraud have been littered with posts from people selling tutorials on how to siphon unemployment insurance funds from different states.
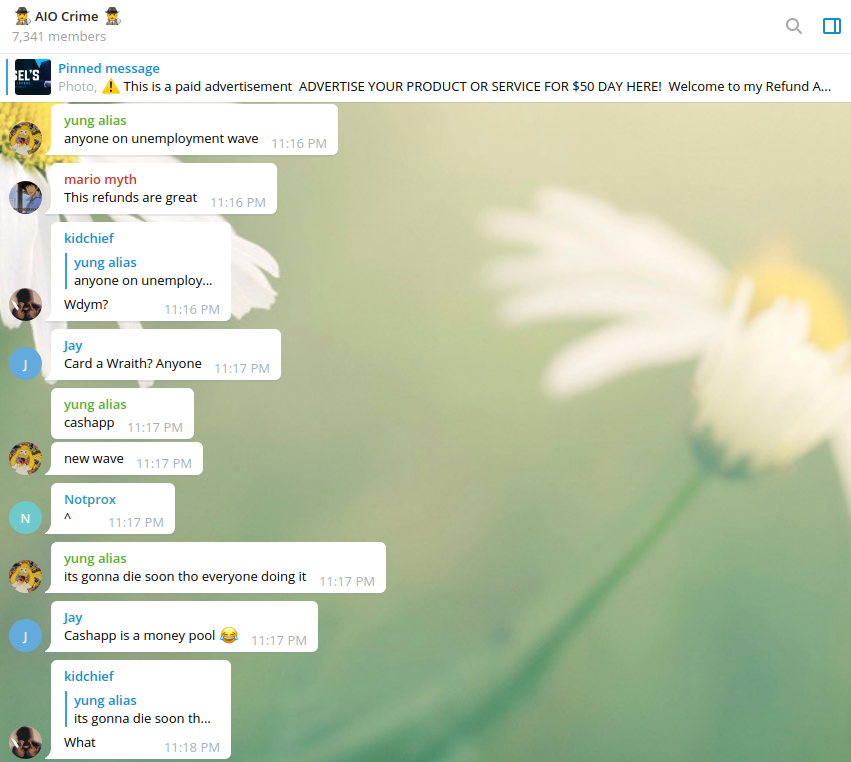
Denizens of a Telegram chat channel newly rededicated to stealing state unemployment funds discussing cashout methods.
Yes, for roughly $50 worth of bitcoin, you too can quickly jump on the unemployment fraud “wave” and learn how to swindle unemployment insurance money from different states. The channel pictured above and others just like it are selling different “methods” for defrauding the states, complete with instructions on how best to avoid getting your phony request flagged as suspicious.
Although, at the rate people in these channels are “flexing” — bragging about their fraudulent earnings with screenshots of recent multiple unemployment insurance payment deposits being made daily — it appears some states aren’t doing a whole lot of fraud-flagging.
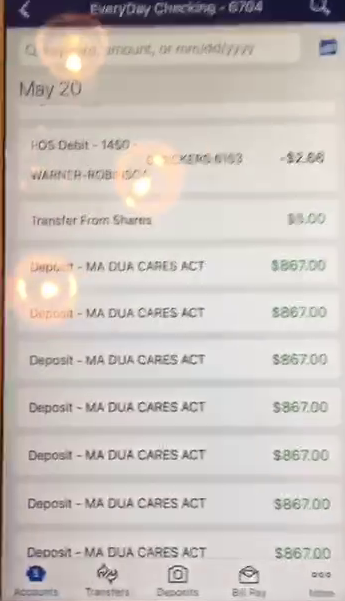
A still shot from a video a fraudster posted to a Telegram channel overrun with people engaged in unemployment insurance fraud shows multiple $800+ payments in one day from Massachusetts’ Department of Unemployment Assistance (DUA).
A federal fraud investigator who’s helping to trace the source of these crimes and who spoke with KrebsOnSecurity on condition of anonymity said many states have few controls in place to spot patterns in fraudulent filings, such as multiple payments going to the same bank accounts, or filings made for different people from the same Internet address.
In too many cases, he said, the deposits are going into accounts where the beneficiary name does not match the name on the bank account. Worse still, the source said, many states have dramatically pared back the amount of information required to successfully request an unemployment filing.
“The ones we’re seeing worst hit are the states that aren’t asking where you worked,” the investigator said. “It used to be they’d have a whole list of questions about your previous employer, and you had to show you were trying to find work. But now because of the pandemic, there’s no such requirement. They’ve eliminated any controls they had at all, and now they’re just shoveling money out the door based on Social Security number, name, and a few other details that aren’t hard to find.”
CANARY IN THE GOLDMINE
Earlier this week, email security firm Agari detailed a fraud operation tied to a seasoned Nigerian cybercrime group it dubbed “Scattered Canary,” which has been busy of late bilking states and the federal government out of economic stimulus and unemployment payments. Agari said this group has been filing hundreds of successful claims, all effectively using the same email address.
“Scattered Canary uses Gmail ‘dot accounts’ to mass-create accounts on each target website,” Agari’s Patrick Peterson wrote. “Because Google ignores periods when interpreting Gmail addresses, Scattered Canary has been able to create dozens of accounts on state unemployment websites and the IRS website dedicated to processing CARES Act payments for non-tax filers (freefilefillableforms.com).”
Indeed, the very day the IRS unveiled its site for distributing CARES Act payments last month, KrebsOnSecurity warned that it was very likely to be abused by fraudsters to intercept stimulus payments from U.S. citizens, mainly because the only information required to submit a claim was name, date of birth, address and Social Security number.
Agari notes that since April 29, Scattered Canary has filed at least 174 fraudulent claims for unemployment with the state of Washington.
“Based on communications sent to Scattered Canary, these claims were eligible to receive up to $790 a week for a total of $20,540 over a maximum of 26 weeks,” Peterson wrote. “Additionally, the CARES Act includes $600 in Federal Pandemic Unemployment Compensation each week through July 31. This adds up to a maximum potential loss as a result of these fraudulent claims of $4.7 million.”
STATE WEB SITE WOES
A number of states have suffered security issues with the PUA websites that exposed personal details of citizens filing unemployment insurance claims. Perhaps the most galling example comes from Arkansas, whose site exposed the SSNs, bank account and routing numbers for some 30,000 applicants.
In that instance, The Arkansas Times alerted the state after hearing from a computer programmer who was filing for unemployment on the site and found he could see other applicants’ data simply by changing the site’s URL slightly. State officials reportedly ignored the programmer’s repeated attempts to get them to fix the issue, and when it was covered by the newspaper the state governor accused the person who found it of breaking the law.
Over the past week, several other states have discovered similar issues with their PUA application sites, including Colorado, Illinois, and Ohio.
Tags: Agari, Pandemic Unemployment Assistance, Patrick Peterson, Scattered Canary, secret service
You can skip to the end and leave a comment. Pinging is currently not allowed.
Courtesy of: krebsonsecurity.com