Suspended Sentence for Mirai Botmaster Daniel Kaye
Last month, KrebsOnSecurity identified U.K. citizen Daniel Kaye as the likely real-life identity behind a hacker responsible for clumsily wielding a powerful botnet built on Mirai, a malware strain that enslaves poorly secured Internet of Things (IoT) devices for use in large-scale online attacks. Today, a German court issued a suspended sentence for Kaye, who now faces cybercrime charges in the United Kingdom.
Daniel Kaye’s Facebook profile page.
In February 2017, authorities in the United Kingdom arrested a 29-year-old U.K. man on suspicion of knocking more than 900,000 Germans offline in a Mirai attack in November 2016. Shortly after that 2016 attack, a hacker using the nickname “Bestbuy” told reporters he was responsible for the outage, apologizing for the incident.
Prosecutors in Europe had withheld Kaye’s name from the media throughout the trial. But a court in Germany today confirmed Kaye’s identity as it handed down a suspended sentence on charges stemming from several failed attacks from his Mirai botnet — which nevertheless caused extensive internet outages for ISPs in the U.K., Germany and Liberia last year.
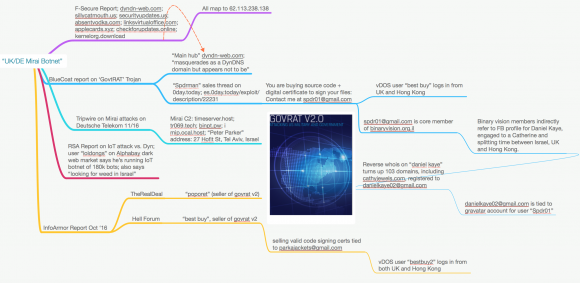
On July 5, KrebsOnSecurity published Who is the GovRAT Author and Mirai Botmaster BestBuy. The story followed clues from reports produced by a half-dozen security firms that traced common clues between this BestBuy nickname and an alter-ego, “Spiderman.”
Both identities were connected to the sale of an espionage tool called GovRAT, which is documented to have been used in numerous cyber espionage campaigns against governments, financial institutions, defense contractors and more than 100 corporations.
That July 5 story traced a trail of digital clues left over 10 years back to Daniel Kaye, a 29-year-old man who had dual U.K. and Israeli citizenship and who was engaged to be married to a U.K. woman.
Last week, a 29-year-old identified by media only as “Daniel K” pleaded guilty in a German court for launching the attacks that knocked 900,000 Deutsche Telekom customers offline. Prosecutors said Daniel K sold access to his Mirai botnet as an attack-for-hire service.
The defendant reportedly told the court that the incident was the biggest mistake of his life, and that he took money in exchange for launching attacks in order to help start a new life with his fiancee.
Today, the regional court in the western city of Cologne said it would suspend the sentence of one year and eight months against Kaye, according to a report from Agence France Presse.
While it may seem that Kaye was given a pass by the German court, he is still facing criminal charges in Britain, where authorities have already requested his extradition.
As loyal readers here no doubt know, KrebsOnSecurity last year was massively attacked by the first-ever Mirai botnet — an attack which knocked this site offline for almost four days before it came back online under the protection of Google’s Project Shield service.
In January 2017, this blog published the results of a four-month investigation into who was likely responsible for not only for writing Mirai, but for leaking the source code for the malware — spawning dozens of competing Mirai botnets like the one that Kaye built. To my knowledge, no charges have yet been filed against any of the individuals named in that story.
Tags: Agence France Presse, BestBuy, Daniel Kaye, GovRAT, Liberia, mirai
You can skip to the end and leave a comment. Pinging is currently not allowed.