Dumping Data from Deep-Insert Skimmers
I recently heard from a police detective who was seeking help identifying some strange devices found on two Romanian men caught maxing out stolen credit cards at local retailers. Further inspection revealed the devices to be semi-flexible data transfer wands that thieves can use to extract stolen ATM card data from “deep-insert skimmers,” wafer-thin fraud devices made to be hidden inside of the card acceptance slot on a cash machine.
The investigator agreed to share the photos if I kept his identity out of this story. He told KrebsOnSecurity that the two men were thought to be part of a crime gang active in the northeast United States, and that the almost 4-inch orange plastic wands allow thieves to download data from a deep insert skimmer. Depending on how the deep-insert skimmer is built, thieves may be able to use the wands to retrieve card data without having to remove the skimmer from the throat of the ATM.
Deep insert skimmers are different from typical insert skimmers in that they are placed in various positions within the card reader transport, behind the shutter of a motorized card reader and completely hidden from the consumer at the front of the ATM.
Here’s a look at these insert skimmer wands (for want of a better term):
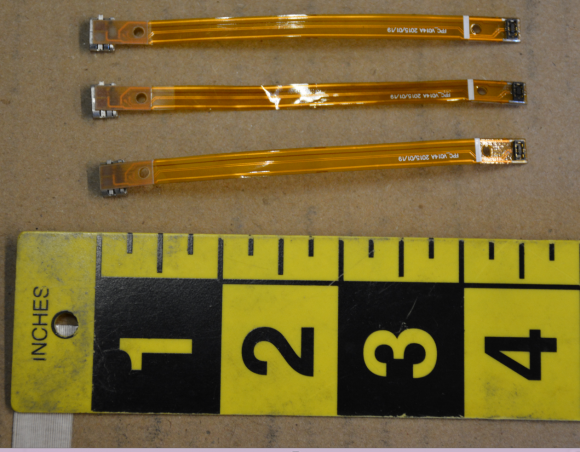
These plastic wands allow thieves to extract stolen card data stored by insert skimmers.
This is what the wand (left) looks like when inserted into a deep-insert skimmer (right):

A data transfer wand inserted into a deep-insert skimmer.
The following image shows three data transfer wands and three insert skimmers seized from compromised ATMs:

Insert skimmers (top) and data transfer wands.
Charlie Harrow, solutions manager for ATM maker NCR Corp., said he has not physically examined the devices pictured above, but that they appear to have a USB interface on one end (the end that plugs into whatever device the crooks use to download stolen card data from the deep-insert skimmer) and a low profile header on the other.
“USB connectors are too big generally to put on a skimmer, especially the newer deep insert skimmers,” Harrow said. “Those devices have very low profile connections such that the overall device thickness is kept to a minimum.”
Once you know about all the ways that skimmer thieves are coming up with to fleece banks and consumers, it’s difficult not to go through life seeing every ATM as potentially compromised. I’m constantly banging and pulling on the poor machines and half expecting half hoping parts to come unglued. I’m always disappointed, but it hasn’t stopped me all the same.
Truthfully, you probably have a better chance of getting physically mugged after withdrawing cash than you do encountering a skimmer in real life. So keep your wits about you when you’re at the ATM, and avoid dodgy-looking and standalone cash machines in low-lit areas, if possible. When possible, stick to ATMs that are physically installed at a bank. And be especially vigilant when withdrawing cash on the weekends; thieves tend to install skimming devices on Saturdays after business hours — when they know the bank won’t be open again for more than 24 hours.
Lastly but most importantly, covering the PIN pad with your hand defeats one key component of most skimmer scams: The spy camera that thieves typically hide somewhere on or near the compromised ATM to capture customers entering their PINs.
Shockingly, few people bother to take this simple, effective step, as detailed in this skimmer tale from 2012, wherein I obtained hours worth of video seized from two ATM skimming operations and saw customer after customer walk up, insert their cards and punch in their digits — all in the clear.
For more on how these insert skimmers work, check out Crooks Go Deep With ‘Deep Insert’ Skimmers. If you’re here because, like me, you find skimmers of all kinds fascinating, please see my series All About Skimmers.
Tags: Charlie Harrow, deep-insert skimmer, NCR Corp
You can skip to the end and leave a comment. Pinging is currently not allowed.
