Mirai Botnet Authors Avoid Jail Time
Citing “extraordinary cooperation” with the government, a court in Alaska on Tuesday sentenced three men to probation, community service and fines for their admitted roles in authoring and using “Mirai,” a potent malware strain used in countless attacks designed to knock Web sites offline — including an enormously powerful attack in 2016 that sidelined this Web site for nearly four days.
The men — 22-year-old Paras Jha Fanwood, New Jersey, Josiah White, 21 of Washington, Pa., and Dalton Norman from Metairie, La. — were each sentenced to five years probation, 2,500 hours of community service, and ordered to pay $127,000 in restitution for the damage caused by their malware.
Mirai enslaves poorly secured “Internet of Things” (IoT) devices like security cameras, digital video recorders (DVRs) and routers for use in large-scale online attacks.
Not long after Mirai first surfaced online in August 2016, White and Jha were questioned by the FBI about their suspected role in developing the malware. At the time, the men were renting out slices of their botnet to other cybercriminals.
Weeks later, the defendants sought to distance themselves from their creation by releasing the Mirai source code online. That action quickly spawned dozens of copycat Mirai botnets, some of which were used in extremely powerful denial-of-service attacks that often caused widespread collateral damage beyond their intended targets.
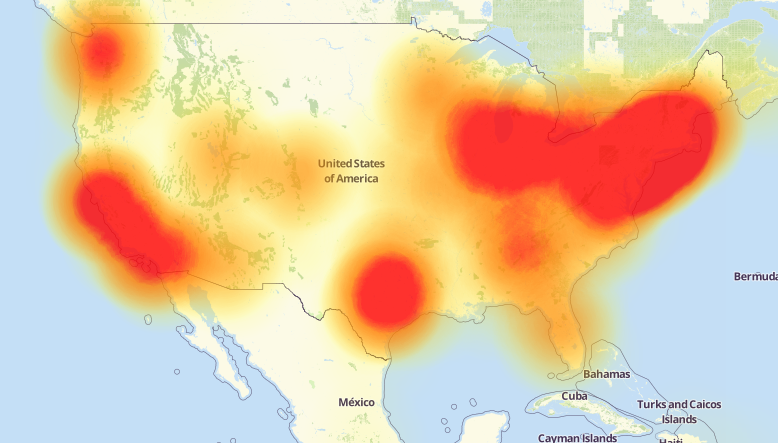
A depiction of the outages caused by the Mirai attacks on Dyn, an Internet infrastructure company. Source: Downdetector.com.
The source code release also marked a period in which the three men began using their botnet for far more subtle and less noisy criminal moneymaking schemes, including click fraud — a form of online advertising fraud that costs advertisers billions of dollars each year.
In September 2016, KrebsOnSecurity was hit with a record-breaking denial-of-service attack from tens of thousands of Mirai-infected devices, forcing this site offline for several days. Using the pseudonym “Anna_Senpai,” Jha admitted to a friend at the time that the attack on this site was paid for by a customer who rented tens of thousands of Mirai-infected systems from the trio.
In January 2017, KrebsOnSecurity published the results of a four-month investigation into Mirai which named both Jha and White as the likely co-authors of the malware. Eleven months later, the U.S. Justice Department announced guilty pleas by Jha, White and Norman.
Prior to Tuesday’s sentencing, the Justice Department issued a sentencing memorandum that recommended lenient punishments for the three men. FBI investigators argued the defendants deserved light sentences because they had provided the government “extraordinary cooperation” in identifying other cybercriminals engaged in related activity and helping to thwart massive cyberattacks on several companies.

Paras Jha, in an undated photo from his former LinkedIn profile.
The government said Jha was especially helpful, devoting hundreds of hours of work in helping investigators. According to the sentencing memo, Jha has since landed a part-time job at at a cybersecurity firm, although the government declined to name his employer.
However, Jha is not quite out of the woods yet: He has also admitted to using Mirai to launch a series of punishing cyberattacks against Rutgers University, where he was enrolled as a computer science student at the time. Jha is slated to be sentenced next week in New Jersey for those crimes.
The Mirai case was prosecuted out of Alaska because the lead FBI agent in the investigation, 36-year-old Special Agent Elliott Peterson, is stationed there. Peterson was able to secure jurisdiction for the case after finding multiple DVRs in Alaska infected with Mirai. Last week, Peterson traveled to Washington, D.C. to join several colleagues in accepting the FBI’s Director Award — the bureau’s highest honor — for the Mirai investigation.
Tags: click fraud, Dalton Norman, Elliott Peterson, fbi, internet of things, IoT, Josiah White, justice department, Mirai botnet, Paras Jha
You can skip to the end and leave a comment. Pinging is currently not allowed.

