Alleged Spam Kingpin ‘Severa’ Extradited to US
Peter Yuryevich Levashov, a 37-year-old Russian computer programmer thought to be one of the world’s most notorious spam kingpins, has been extradited to the United States to face federal hacking and spamming charges.

Levashov, in an undated photo.
Levashov, who allegedly went by the hacker names “Peter Severa,” and “Peter of the North,” hails from St. Petersburg in northern Russia, but he was arrested last year while in Barcelona, Spain with his family.
Authorities have long suspected he is the cybercriminal behind the once powerful spam botnet known as Waledac (a.k.a. “Kelihos”), a now-defunct malware strain responsible for sending more than 1.5 billion spam, phishing and malware attacks each day.
According to a statement released by the U.S. Justice Department, Levashov was arraigned last Friday in a federal court in New Haven, Ct. Levashov’s New York attorney Igor Litvak said he is eager to review the evidence against Mr. Levashov, and that while the indictment against his client is available, the complaint in the case remains sealed.
“We haven’t received any discovery, we have no idea what the government is relying on to bring these allegations,” Litvak said. “Mr. Levashov maintains his innocence and is looking forward to resolving this case, clearing his name, and returning home to his wife and 5-year-old son in Spain.”
In 2010, Microsoft — in tandem with a number of security researchers — launched a combined technical and legal sneak attack on the Waledac botnet, successfully dismantling it. The company would later do the same to the Kelihos botnet, a global spam machine which shared a great deal of computer code with Waledac.
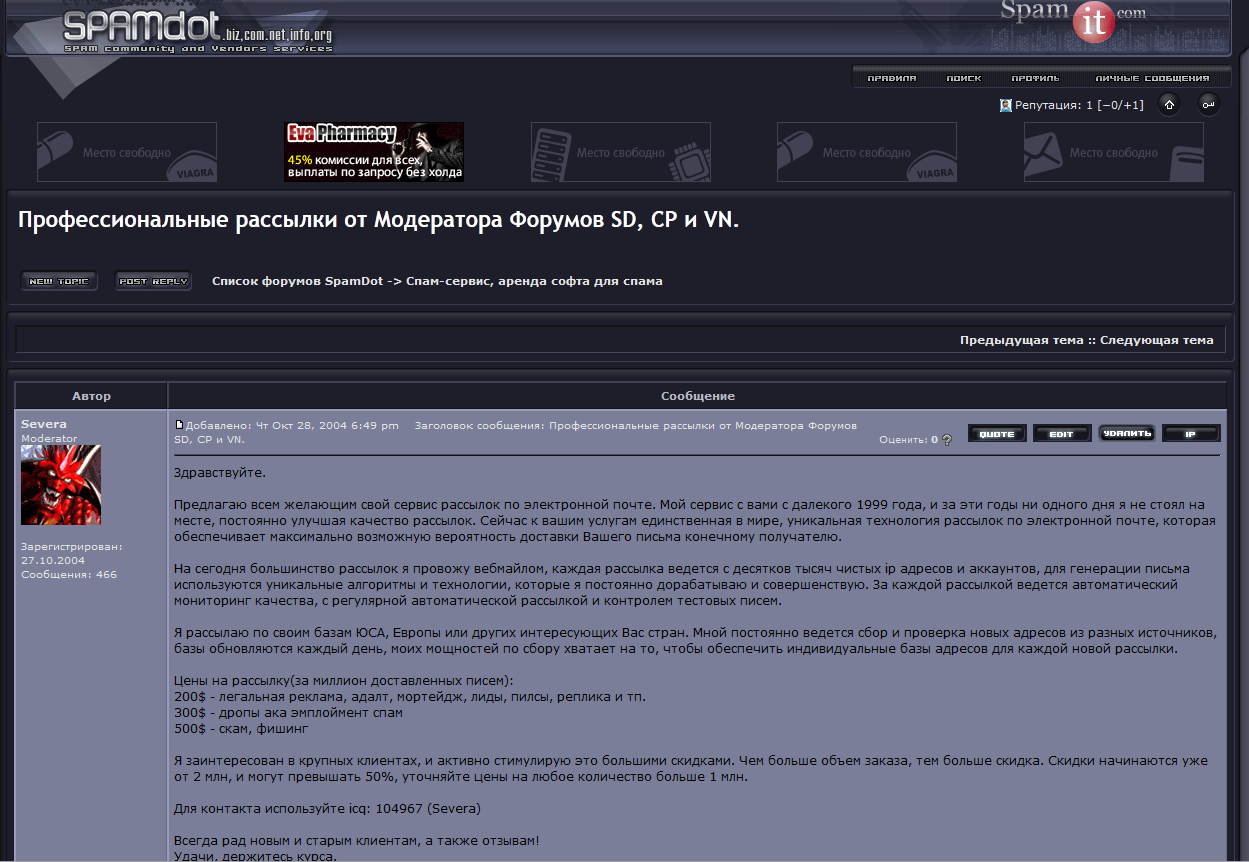
Severa routinely rented out segments of his Waledac botnet to anyone seeking a vehicle for sending spam. For $200, vetted users could hire his botnet to blast one million pieces of spam. Junk email campaigns touting employment or “money mule” scams cost $300 per million, and phishing emails could be blasted out through Severa’s botnet for the bargain price of $500 per million.
Waledac first surfaced in April 2008, but many experts believe the spam-spewing machine was merely an update to the Storm worm, the engine behind another massive spam botnet that first surfaced in 2007. Both Waledac and Storm were major distributors of pharmaceutical and malware spam.
According to Microsoft, in one month alone approximately 651 million spam emails attributable to Waledac/Kelihos were directed to Hotmail accounts, including offers and scams related to online pharmacies, imitation goods, jobs, penny stocks, and more. The Storm worm botnet also sent billions of messages daily and infected an estimated one million computers worldwide.
Both Waledac/Kelihos and Storm were hugely innovative because they each included self-defense mechanisms designed specifically to stymie security researchers who might try to dismantle the crime machines.
Waledac and Storm sent updates and other instructions via a peer-to-peer communications system not unlike popular music and file-sharing services. Thus, even if security researchers or law-enforcement officials manage to seize the botnet’s back-end control servers and clean up huge numbers of infected PCs, the botnets could respawn themselves by relaying software updates from one infected PC to another.
FAKE NEWS
According to a lengthy April 2017 story in Wired.com about Levashov’s arrest and the takedown of Waledac, Levashov got caught because he violated a basic security no-no: He used the same log-in credentials to both run his criminal enterprise and log into sites like iTunes.
After Levashov’s arrest, numerous media outlets quoted his wife saying he was being rounded up as part of a dragnet targeting Russian hackers thought to be involved in alleged interference in the 2016 U.S. election. Russian news media outlets made much hay over this claim. In contesting his extradition to the United States, Levashov even reportedly told the RIA Russian news agency that he worked for Russian President Vladimir Putin‘s United Russia party, and that he would die within a year of being extradited to the United States.
“If I go to the U.S., I will die in a year,” Levashov is quoted as saying. “They want to get information of a military nature and about the United Russia party. I will be tortured, within a year I will be killed, or I will kill myself.”
But there is so far zero evidence that anyone has accused Levashov of being involved in election meddling. However, the Waledac/Kelihos botnet does have a historic association with election meddling: It was used during the Russian election in 2012 to send political messages to email accounts on computers with Russian Internet addresses. Those emails linked to fake news stories saying that Mikhail D. Prokhorov, a businessman who was running for president against Putin, had come out as gay.
SEVERA’S PARTNERS
If Levashov was to plead guilty in the case being prosecuted by U.S. authorities, it could shed light on the real-life identities of other top spammers.
Severa worked very closely with two major purveyors of spam. One was Alan Ralsky, an American spammer who was convicted in 2009 of paying him and other spammers to promote the pump-and-dump stock scams.
The other was a spammer who went by the nickname “Cosma,” the cybercriminal thought to be responsible for managing the Rustock botnet (so named because it was a Russian botnet frequently used to send pump-and-dump stock spam). In 2011, Microsoft offered a still-unclaimed $250,000 reward for information leading to the arrest and conviction of the Rustock author.
Microsoft believes Cosma’s real name may be Dmitri A. Sergeev, Artem Sergeev, or Sergey Vladomirovich Sergeev. In June 2011, KrebsOnSecurity published a brief profile of Cosma that included Sergeev’s resume and photo, both of which indicated he is a Belorussian programmer who once sought a job at Google. For more on Cosma, see “Flashy Car Got Spam Kingpin Mugged.”
Severa and Cosma had met one another several times in their years together in the stock spamming business, and they appear to have known each other intimately enough to be on a first-name basis. Both of these titans of junk email are featured prominently in “Meet the Spammers,” the 7th chapter of my book, Spam Nation: The Inside Story of Organized Cybercrime.
Much like his close associate — Cosma, the Rustock botmaster — Severa may also have a $250,000 bounty on his head, albeit indirectly. The Conficker worm, a global contagion launched in 2009 that quickly spread to an estimated 9 to 15 million computers worldwide, prompted an unprecedented international response from security experts. This group of experts, dubbed the “Conficker Cabal,” sought in vain to corral the spread of the worm.
But despite infecting huge numbers of Microsoft Windows systems, Conficker was never once used to send spam. In fact, the only thing that Conficker-infected systems ever did was download and spread a new version of the the malware that powered the Waledac botnet. Later that year, Microsoft announced it was offering a $250,000 reward for information leading to the arrest and conviction of the Conficker author(s). Some security experts believe this proves a link between Severa and Conficker.
Both Cosma and Severa were quite active on Spamit[dot]com, a once closely-guarded forum for Russian spammers. In 2010, Spamit was hacked, and a copy of its database was shared with this author. In that database were all private messages between Spamit members, including many between Cosma and Severa. For more on those conversations, see “A Closer Look at Two Big Time Botmasters.”
In addition to renting out his spam botnet, Severa also managed multiple affiliate programs in which he paid other cybercriminals to distribute so-called fake antivirus products. Also known as “scareware,” fake antivirus was at one time a major scourge, using false and misleading pop-up alerts to trick and mousetrap unsuspecting computer users into purchasing worthless (and in many cases outright harmful) software disguised as antivirus software.
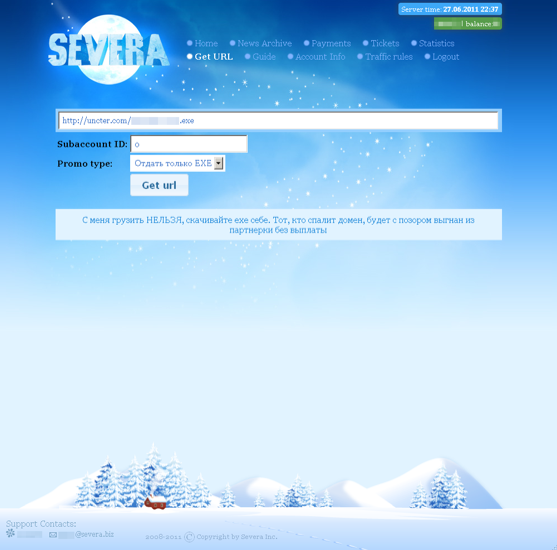
A screenshot of the eponymous scareware affiliate program run by “Severa,” allegedly the cybercriminal alias of Peter Levashov.
In 2011, KrebsOnSecurity published Spam & Fake AV: Like Ham & Eggs, which sought to illustrate the many ways in which the spam industry and fake antivirus overlapped. That analysis included data from Brett Stone-Gross, a cybercrime expert who later would assist Microsoft and other researchers in their successful efforts to dismantle the Waledac/Kelihos botnet.
Levashov faces federal criminal charges on eight counts, including aggravated identity theft, wire fraud, conspiracy, and intentional damage to protected computers. The indictment in his case is available here (PDF).
Further reading: Mr Waledac — The Peter North of Spamming
Tags: Alan Ralsky, Artem Sergeev, Conficker, Cosma, Dmitri A. Sergeev, fake news, Kelihos, Mikhail D. Prokhorov, Peter Severa, Pyotr Yuryevich Levashov, Sergey Vladomirovich Sergeev, Severa, Spam Nation, Spamit, Vladimir V. Putin, waledac, wired.com
You can skip to the end and leave a comment. Pinging is currently not allowed.