Hacked Password Service Leakbase Goes Dark
Leakbase, a Web site that indexed and sold access to billions of usernames and passwords stolen in some of the world largest data breaches, has closed up shop. A source close to the matter says the service was taken down in a law enforcement sting that may be tied to the Dutch police raid of the Hansa dark web market earlier this year.
Leakbase[dot]pw began selling memberships in September 2016, advertising more than two billion usernames and passwords that were stolen in high-profile breaches at sites like linkedin.com, myspace.com and dropbox.com.
But roughly two weeks ago KrebsOnSecurity began hearing from Leakbase users who were having trouble reaching the normally responsive and helpful support staff responsible for assisting customers with purchases and site issues.
Sometime this weekend, Leakbase began redirecting visitors to haveibeenpwned.com, a legitimate breach alerting service run by security researcher Troy Hunt (Hunt’s site lets visitors check if their email address has shown up in any public database leaks, but it does not store corresponding account passwords).
Leakbase reportedly came under new ownership after its hack in April. According to a source with knowledge of the matter but who asked to remain anonymous, the new owners of Leakbase dabbled in dealing illicit drugs at Hansa, a dark web marketplace that was dismantled in July by authorities in The Netherlands.
The Dutch police had secretly seized Hansa and operated it for a time in order to gather more information about and ultimately arrest many of Hansa’s top drug sellers and buyers.
According to my source, information the Dutch cops gleaned from their Hansa takeover led authorities to identify and apprehend one of the owners of Leakbase. This information could not be confirmed, and the Dutch police have not yet responded to requests for comment.
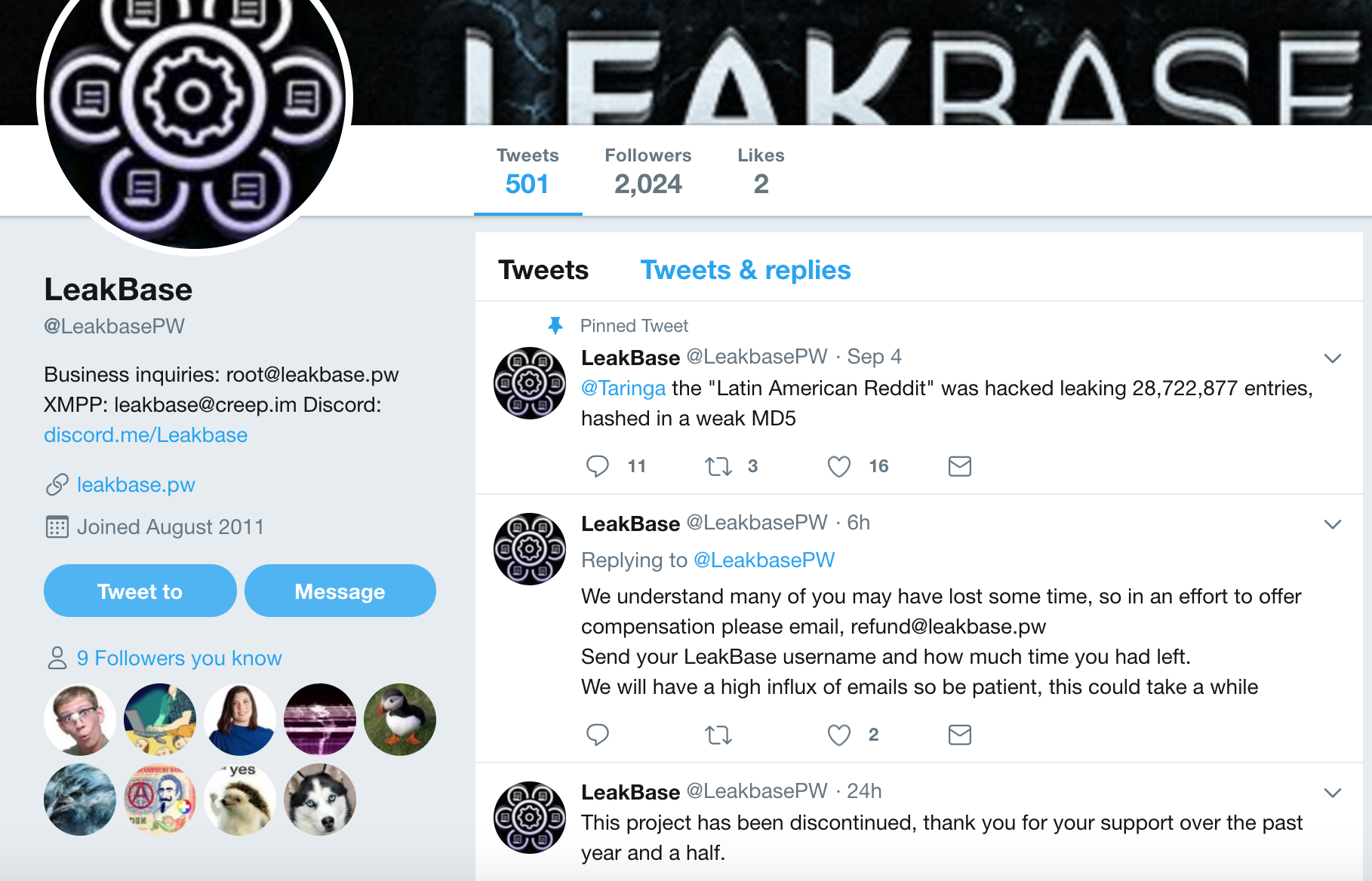
A message posted Dec. 2 to Leakbase’s Twitter account states that the service was being discontinued, and the final message posted to that account seems to offer paying customers some hope of recovering any unused balances stored with the site.
“We understand many of you may have lost some time, so in an effort to offer compensation please email, refund@leakbase.pw Send your LeakBase username and how much time you had left,” the message reads. “We will have a high influx of emails so be patient, this could take a while.”
My source noted that these last two messages are interesting because they are unlike every other update posted to the Leakbase Twitter account. Prior to the shutdown message on Dec. 2, all updates to that account were done via Twitter’s Web client; but the last two were sent via Mobile Web (M2).
Ironically, Leakbase was itself hacked back in April 2017 after a former administrator was found to be re-using a password from an account at x4b[dot]net, a service that Leakbase relied upon at the time to protect itself from distributed denial-of-service (DDoS) attacks intended to knock the site offline.
X4B[dot]net was hacked just days before the Leakbase intrusion, and soon after cleartext passwords and usernames from hundreds of Leakbase users were posted online by the hacker group calling itself the Money Team.
Many readers have questioned how it could be illegal to resell passwords that were leaked online in the wake of major data breaches. The argument here is generally that in most cases this information is already in the public domain and thus it can’t be a crime to index and resell it.
However, many legal experts see things differently. In February 2017, I wrote about clues that tied back to a real-life identity for one of the alleged administrators of Leakedsource, a very similar service (it’s worth noting that the subject of that story also was found out because he re-used the same credentials across multiple sites).
In the Leakedsource story, I interviewed Orin Kerr, director of the Cybersecurity Law Initiative at The George Washington University. Kerr told me that owners of services like Leakbase and Leakedsource could face criminal charges if prosecutors could show these services intended for the passwords that are for sale on the site to be used in the furtherance of a crime.
Kerr said trafficking in passwords is clearly a crime under the Computer Fraud and Abuse Act (CFAA).
Specifically, Section A6 of the CFAA, which makes it a crime to “knowingly and with intent to defraud traffic in any password or similar information through which a computer may be accessed without authorization, if…such trafficking affects interstate or foreign commerce.”
“CFAA quite clearly punishes password trafficking,” Kerr said. “The statute says the [accused] must be trafficking in passwords knowingly and with intent to defraud, or trying to further unauthorized access.”
Tags: CFAA, Cybersecurity Law Institute, Hansa, HaveIBeenPwned.com, leakbase, Money Team, Orin Kerr, Troy Hunt, x4b hack
You can skip to the end and leave a comment. Pinging is currently not allowed.