Surreptitious cryptocurrency miners hide on Politifact and hundreds of other sites

Politifact is the latest and perhaps most high-profile website to have hosted code that secretly hijacks visitors’ CPUs to mine cryptocurrency. Driven by a boom in cryptocoin value and a lack of protections against JavaScript routines like this one, this surprising form of audience monetization is now found on hundreds of sites.
(Update: Politifact has removed the code and is looking into how it got there.)
It’s not quite an ad, and it’s not quite malware, nor is it strictly speaking a virus or exploit. JavaScript is used for all kinds of things in the background of practically every major website, from tracking users to displaying custom fonts. Generally speaking, these apps are running code hosted on another server that the end user can’t inspect, and often doesn’t even realize their browser is executing.
In recent months, several JavaScript-based cryptocurrency miners have appeared. The idea, supposedly, is that instead of showing your visitors ads, you have their CPU run the calculations necessary to mine a currency like Bitcoin. As the administrator, you could control the CPU load and reap any resulting coins. CoinHive is a new business that offers this as a service.
Predictably, this already questionable approach to monetization has already been repurposed by malicious actors. Injecting a bit of JavaScript into the front page of a website is often simpler to do than penetrate its databases or phish its admins; and once it’s in, it runs itself — all you have to do is give it a wallet to put the coins in.
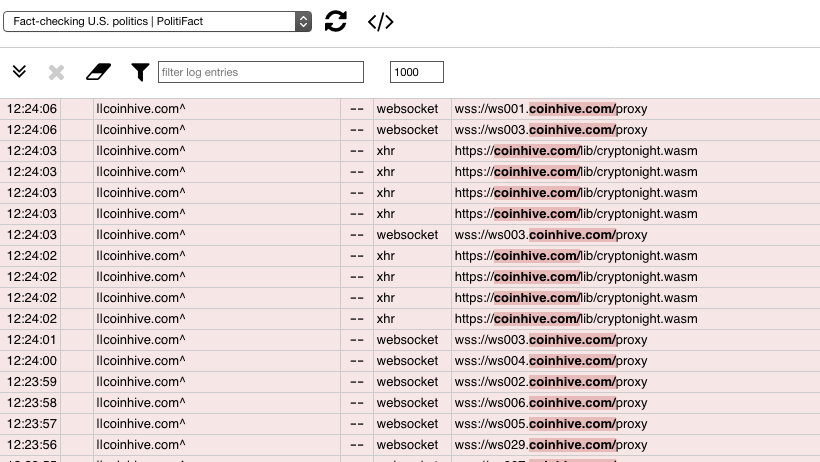 That seems to be what happened at Politifact; my blocker registers a CoinHive instance on the main pages of the site, with new requests coming in multiple times a second. Inspecting the site’s JavaScript shows an enormous chunk of CoinHive miner code sitting amongst the ordinary scripts. It’s pretty hard to miss, and if not blocked it takes over the whole CPU until the tab is closed. With a few million users mining for a minute or two each while they check out the latest political shenanigans, those cycles add up quick.
That seems to be what happened at Politifact; my blocker registers a CoinHive instance on the main pages of the site, with new requests coming in multiple times a second. Inspecting the site’s JavaScript shows an enormous chunk of CoinHive miner code sitting amongst the ordinary scripts. It’s pretty hard to miss, and if not blocked it takes over the whole CPU until the tab is closed. With a few million users mining for a minute or two each while they check out the latest political shenanigans, those cycles add up quick.
I’ve contacted the site’s team to ask what the story is; someone there told The Register that they’re looking into it, but I’ll update if I hear back with more details.
The site is far from alone: a study by ad blocker company AdGuard showed that hundreds of sites, most of them on the shady site (porn and torrent sites, for instance) are running CoinHive code, or some other JavaScript-based miner.
What can you do? Well, this is a great reason to install an ad blocker, if you haven’t already: in addition to getting rid of intrusive ads and trackers, some of them block unknown scripts or have a blacklist of known malicious ones. I use uBlock Origin, which also makes it easy to whitelist sites (like this one) that only feature organic, free-range advertisements. But you could also use NoScript, AdBlock or any one of the many out there, depending on your platform and browser.