P2P Weakness Exposes Millions of IoT Devices
A peer-to-peer (P2P) communications technology built into millions of security cameras and other consumer electronics includes several critical security flaws that expose the devices to eavesdropping, credential theft and remote compromise, new research has found.
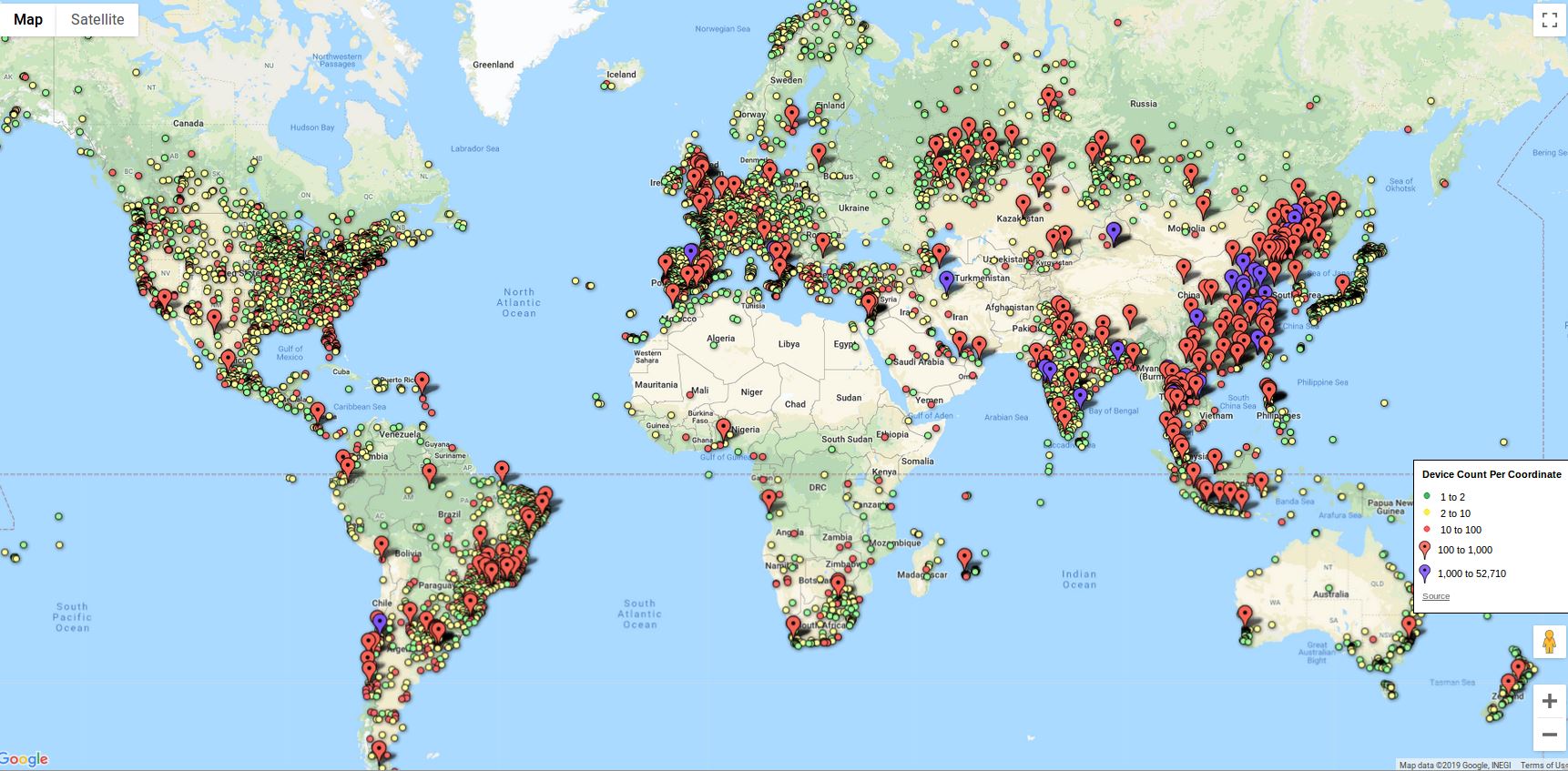
A map showing the distribution of some 2 million iLinkP2P-enabled devices that are vulnerable to eavesdropping, password theft and possibly remote compromise, according to new research.
The security flaws involve iLnkP2P, software developed by China-based Shenzhen Yunni Technology. iLnkP2p is bundled with millions of Internet of Things (IoT) devices, including security cameras and Webcams, baby monitors, smart doorbells, and digital video recorders.
iLnkP2P is designed to allow users of these devices to quickly and easily access them remotely from anywhere in the world, without having to tinker with one’s firewall: Users simply download a mobile app, scan a barcode or enter the six-digit ID stamped onto the bottom of the device, and the P2P software handles the rest.
But according to an in-depth analysis shared with KrebsOnSecurity by security researcher Paul Marrapese, iLnkP2P devices offer no authentication or encryption and can be easily enumerated, allowing potential attackers to establish a direct connection to these devices while bypassing any firewall restrictions.
Marrapese said a proof-of-concept script he built identified more than two million vulnerable devices around the globe (see map above). He found that 39 percent of the vulnerable IoT things were in China; another 19 percent are located in Europe; seven percent of them are in use in the United States.
Although it may seem impossible to enumerate more than a million devices with just a six-digit ID, Marrapese notes that each ID begins with a unique alphabetic prefix that identifies which manufacturer produced the device, and there are dozens of companies that white-label the iLnkP2P software.
For example, HiChip — a Chinese IoT vendor that Marrapese said accounts for nearly half of the vulnerable devices — uses the prefixes FFFF, GGGG, HHHH, IIII, MMMM, ZZZZ.
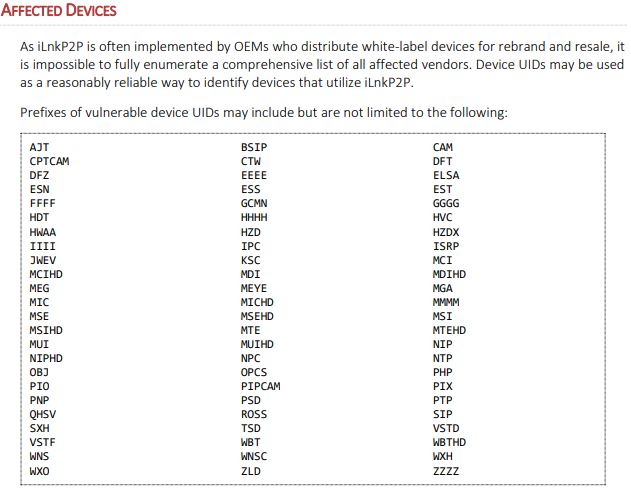
These prefixes identify different product lines and vendors that use iLnkP2P. If the code stamped on your IoT device begins with one of these, it is vulnerable.
“In theory, this allows them to support nearly 6 million devices for these prefixes alone,” Marrapese said. “In reality, enumeration of these prefixes has shown that the number of online devices was ~1,517,260 in March 2019. By enumerating all of the other vendor prefixes, that pushes the number toward 2 million.”
Marrapese said he also built a proof-of-concept attack that can steal passwords from devices by abusing their built-in “heartbeat” feature. Upon being connected to a network, iLnkP2P devices will regularly send a heartbeat or “here I am” message to their preconfigured P2P servers and await further instructions.
“A P2P server will direct connection requests to the origin of the most recently-received heartbeat message,” Marrapese said. “Simply by knowing a valid device UID, it is possible for an attacker to issue fraudulent heartbeat messages that will supersede any issued by the genuine device. Upon connecting, most clients will immediately attempt to authenticate as an administrative user in plaintext, allowing an attacker to obtain the credentials to the device.”
To make matters worse, even if an attacker doesn’t want to bother intercepting device passwords, a great many of them will be running in their factory-default state with the factory-default password. The IoT malware Mirai proved this conclusively, as it rapidly spread to millions of devices using nothing more than the default credentials for IoT devices made by dozens of manufacturers.
What’s more, as we saw with Mirai the firmware and software built into these IoT devices is often based on computer code that is many years old and replete with security vulnerabilities, meaning that anyone able to communicate directly with them is also likely to be able to remotely compromise them with malicious software.
Marrapese said despite attempts to notify China’s CERT, iLnk and a half dozen major vendors whose products make up the bulk of the affected devices, none of them have responded to his reports — even though he first started reaching out to them more than four months ago. Neither HiChip nor iLnk responded to requests for comment sent by KrebsOnSecurity.
Interestingly, iLnk’s Web site (p1.i-lnk[.]com) currently appears to be non-functional, and a review of its HTML source code indicates the site is currently compromised by an obfuscated script that tries to redirect visitors to a Chinese gaming Web site.
Despite the widespread impact of these vulnerabilities, Marrapese’s research suggests that remediation from vendors is unlikely – and in fact, unfeasible.
“The nature of these vulnerabilities makes them extremely difficult to remediate for several reasons,” Marrapese wrote. “Software-based remediation is unlikely due to the infeasibility of changing device UIDs, which are permanently assigned during the manufacturing process. Furthermore, even if software patches were issued, the likelihood of most users updating their device firmware is low. Physical device recalls are unlikely as well because of considerable logistical challenges. Shenzhen Yunni Technology is an upstream vendor with inestimable sub-vendors due to the practice of white-labeling and reselling.”
Marrapese said there is no practical way to turn off the P2P functionality on the affected devices. Many IoT devices can punch holes in firewalls using a feature built into hardware-based routers called Universal Plug and Play (UPnP). But simply turning off UPnP on one’s router won’t prevent the devices from establishing a P2P connection as they rely on a different communications technique called “UDP hole punching.”
Marrapese said it should be possible to block vulnerable devices from communicating with any P2P servers by setting up firewall rules that block traffic destined for UDP port 32100.
However, a much safer idea would be to simply avoid purchasing or using IoT devices that advertise any P2P capabilities. Previous research has unearthed similar vulnerabilities in the P2P functionality built into other IoT systems. For examples of this, see This is Why People Fear the Internet of Things, and Researchers Find Fresh Fodder for IoT Attack Cannons.
Marrapese documented his findings in more detail here. The enumeration vulnerability has been assigned CVE-2019-11219, and the man-in-the-middle vulnerability has been assigned CVE-2019-11220.
Additional reading: Some Basic Rules for Securing your IoT Stuff.
Tags: HiChip, iLnkP2P, P2P, Paul Marrapese, Shenzhen Yunni Technology, UDP hole punching, UPnP
You can skip to the end and leave a comment. Pinging is currently not allowed.