Microsoft Patches ‘Wormable’ Flaw in Windows XP, 7 and Windows 2003
Microsoft today is taking the unusual step of releasing security updates for unsupported but still widely-used Windows operating systems like XP and Windows 2003, citing the discovery of a “wormable” flaw that the company says could be used to fuel a fast-moving malware threat like the WannaCry ransomware attacks of 2017.
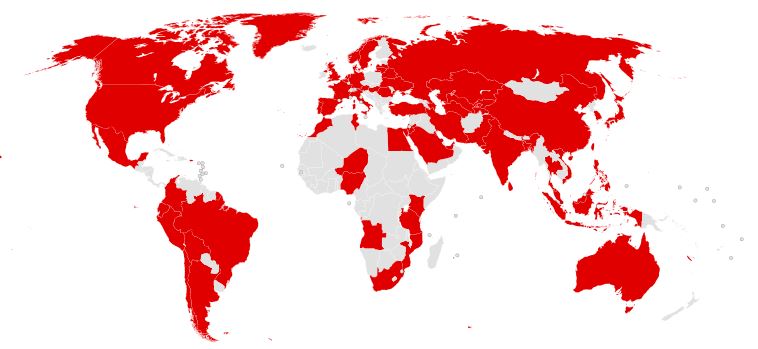
The May 2017 global malware epidemic WannaCry affected some 200,000 Windows systems in 150 countries. Source: Wikipedia.
The vulnerability (CVE-2019-0708) resides in the “remote desktop services” component built into supported versions of Windows, including Windows 7, Windows Server 2008 R2, and Windows Server 2008. It also is present in computers powered by Windows XP and Windows 2003, operating systems for which Microsoft long ago stopped shipping security updates.
Microsoft said the company has not yet observed any evidence of attacks against the dangerous security flaw, but that it is trying to head off a serious and imminent threat.
“While we have observed no exploitation of this vulnerability, it is highly likely that malicious actors will write an exploit for this vulnerability and incorporate it into their malware,” wrote Simon Pope, director of incident response for the Microsoft Security Response Center.
“This vulnerability is pre-authentication and requires no user interaction,” Pope said. “In other words, the vulnerability is ‘wormable,’ meaning that any future malware that exploits this vulnerability could propagate from vulnerable computer to vulnerable computer in a similar way as the WannaCry malware spread across the globe in 2017. It is important that affected systems are patched as quickly as possible to prevent such a scenario from happening.”
The WannaCry ransomware threat spread quickly across the world in May 2017 using a vulnerability that was particularly prevalent among systems running Windows XP and older versions of Windows. Microsoft had already released a patch for the flaw, but many older and vulnerable OSes were never updated. Europol estimated at the time that WannaCry spread to some 200,000 computers across 150 countries.
CVE-2019-0708 does not affect Microsoft’s latest operating systems — Windows 10, Windows 8.1, Windows 8, Windows Server 2019, Windows Server 2016, Windows Server 2012 R2, or Windows Server 2012.
More information on how to download and deploy the update for CVE-2019-0708 is here.
All told, Microsoft today released 16 updates targeting at least 79 security holes in Windows and related software — nearly a quarter of them earning Microsoft’s most dire “critical” rating. Critical bugs are those that can be exploited by malware or ne’er-do-wells to break into vulnerable systems remotely, without any help from users.
One of those critical updates fixes a zero-day vulnerability — (CVE-2019-0863) in the Windows Error Reporting Service — that’s already been seen in targeted attacks, according to Chris Goettl, director of product management for security vendor Ivanti.
Other Microsoft products receiving patches today including Office and Office365, Sharepoint, .NET Framework and SQL server. Once again — for the fourth time this year — Microsoft is patching yet another critical flaw in the Windows component responsible for assigning Internet addresses to host computers (a.k.a. “Windows DHCP client”).
“Any unauthenticated attacker who can send packets to a DHCP server can exploit this vulnerability,” to deliver a malicious payload, notes Jimmy Graham at Qualys.
Staying up-to-date on Windows patches is good. Updating only after you’ve backed up your important data and files is even better. A good backup means you’re not pulling your hair out if the odd buggy patch causes problems booting the system. So do yourself a favor and backup your files before installing any patches.
Note that Windows 10 likes to install patches all in one go and reboot your computer on its own schedule. Microsoft doesn’t make it easy for Windows 10 users to change this setting, but it is possible. For all other Windows OS users, if you’d rather be alerted to new updates when they’re available so you can choose when to install them, there’s a setting for that in Windows Update.
 As per usual, Adobe has released security fixes for Flash Player and Acrobat/Reader. The Flash Player update fixes a single, critical bug in the program. Adobe’s Acrobat/Reader update plugs at least 84 security holes.
As per usual, Adobe has released security fixes for Flash Player and Acrobat/Reader. The Flash Player update fixes a single, critical bug in the program. Adobe’s Acrobat/Reader update plugs at least 84 security holes.
Microsoft Update should install the Flash fix by default, along with the rest of this month’s patch bundle. Fortunately, the most popular Web browser by a long shot — Google Chrome — auto-updates Flash but also is now making users explicitly enable Flash every time they want to use it. By the summer of 2019 Google will make Chrome users go into their settings to enable it every time they want to run it.
Firefox also forces users with the Flash add-on installed to click in order to play Flash content; instructions for disabling or removing Flash from Firefox are here. Adobe will stop supporting Flash at the end of 2020.
As always, if you experience any problems installing any of these patches this month, please feel free to leave a comment about it below; there’s a good chance other readers have experienced the same and may even chime in here with some helpful tips.
Tags: Chris Goettl, CVE-2019-0708, DHCP, Flash Player, Ivanti, Qualys, WannaCry, Windows 2003, Windows XP
You can skip to the end and leave a comment. Pinging is currently not allowed.