A Breach, or Just a Forced Password Reset?
Software giant Citrix Systems recently forced a password reset for many users of its Sharefile content collaboration service, warning it would be doing this on a regular basis in response to password-guessing attacks that target people who re-use passwords across multiple Web sites. Many Sharefile users interpreted this as a breach at Citrix and/or Sharefile, but the company maintains that’s not the case. Here’s a closer look at what happened, and some ideas about how to avoid a repeat of this scenario going forward.
The notice sent to ShareFile users looked like this:
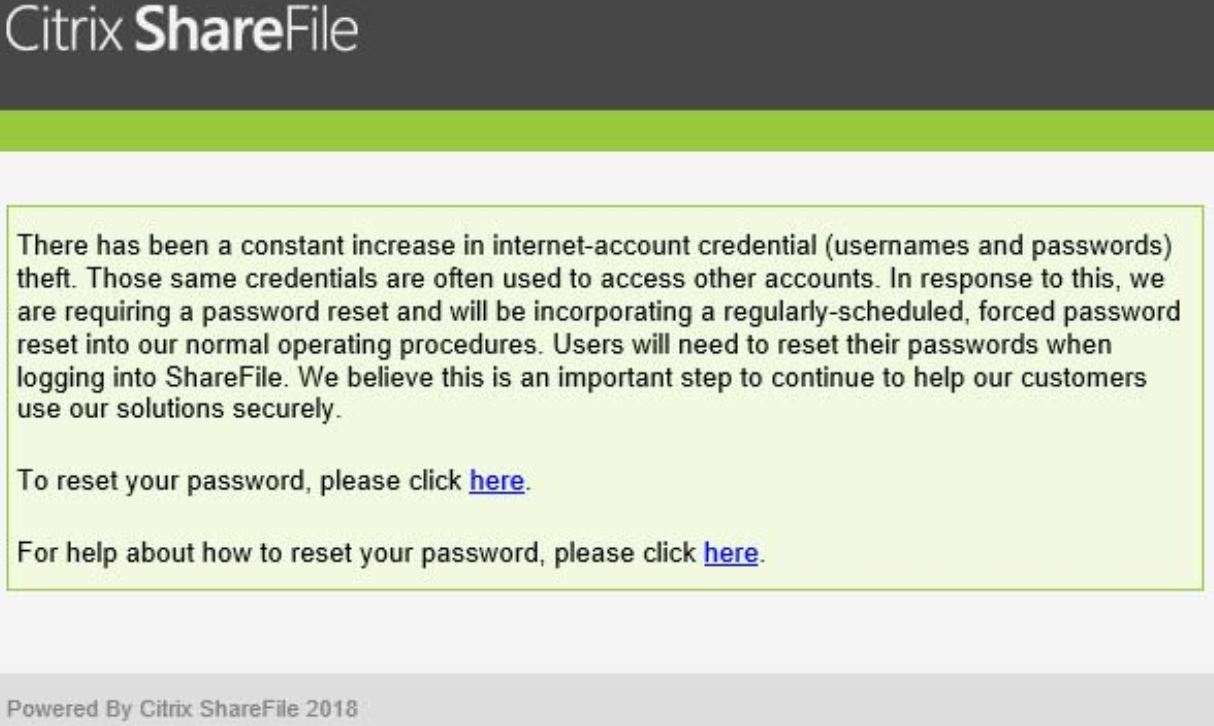
Dozens of readers forwarded the above message to KrebsOnSecurity, saying they didn’t understand the reasoning for the mass password reset and that they suspected a breach at ShareFile.
I reached out to ShareFile and asked them point blank whether this reset effort was in response to any sort of intrusion at Citrix or ShareFile; they said no. I asked if this notice had been sent to everyone, and inquired whether ShareFile offers any form(s) of multi-factor authentication options that customers could use to supplement the security of passwords.
A Citrix spokesperson referred me to this page, which says ShareFile users have a number of options when it comes to locking down their accounts with multi-factor authentication, including a one-time code sent via SMS/text message, as well as one-time passwords generated by support authenticator mobile apps from Google and Microsoft (app-based multi-factor is the more secure option, as discussed here).
More importantly, the Citrix spokesperson said the company did not enforce a password reset on accounts that were using its most robust form of multi-factor authentication (single sign-on solutions, or SSOs). To wit:
“This is not in response to a breach of Citrix products or services,” wrote spokesperson Jamie Buranich. “Citrix forced password resets with the knowledge that attacks of this nature historically come in waves. Attacker’s additional efforts adapt to the results, often tuning the volume and approach of their methods. Our objective was to minimize the risk to our customers. We did not enforce a password reset on accounts that are using more stringent authentication controls. Citrix also directly integrates with common SSO solutions, which significantly reduces risk.”
The company did not respond to questions about why it decided to adopt regular password resets as a policy when doing so flies in the face of password and authentication best practices recommended by the National Institute of Standards and Technology (NIST), which warns:
“Verifiers SHOULD NOT require memorized secrets to be changed arbitrarily (e.g., periodically). However, verifiers SHALL force a change if there is evidence of compromise of the authenticator.”
NIST explains its rationale for steering organizations away from regular forced password resets thusly:
“Users tend to choose weaker memorized secrets when they know that they will have to change them in the near future. When those changes do occur, they often select a secret that is similar to their old memorized secret by applying a set of common transformations such as increasing a number in the password. This practice provides a false sense of security if any of the previous secrets has been compromised since attackers can apply these same common transformations.”
“But if there is evidence that the memorized secret has been compromised, such as by a breach of the verifier’s hashed password database or observed fraudulent activity, subscribers should be required to change their memorized secrets. However, this event-based change should occur rarely, so that they are less motivated to choose a weak secret with the knowledge that it will only be used for a limited period of time.”
In short, NIST says it makes sense to force an across-the-board password reset following a breach — either of a specific user’s account or the entire password database. But doing so at regular intervals absent such evidence of compromise is likely to result in less complex and secure passwords.
Ideally, ShareFile users who received a password reset notice may be able to avoid the next round of password resets by adopting one of the two-step authentication options mentioned above. And I hope it goes without saying, but please don’t re-use a password you used anywhere else.
However, if you are the type of person who likes to re-use passwords, then you definitely need to be using a password manager, which helps you pick and remember strong passwords/passphrases and essentially lets you use the same strong master password/passphrase across all Web sites.
Incidentally, there are several companies — such as auth0 and Okta — that make it easy to integrate with breached password databases like Troy Hunt’s HaveIBeenPwned.com to help proactively prevent users from picking passwords they have used at other sites (or at least at other sites that have been breached publicly).
Whether online merchants are willing to adopt such preemptive approaches is another matter, said Julie Conroy, research director with the Aite Group, a market analyst firm.
“With the reality that such a vast swath of username/password combinations have been compromised, this creates the potential for a ton of inline friction, something that is an anathema to merchants, and which banks work hard to stay away from as well,” Conroy said.
Update: 4:53 p.m. ET: Citrix just published its own blog post about this here.
Tags: Aite Group, auth0, Citrix, HaveIBeenPwned.com, Jamie Buranich, Julie Conroy, Okta, ShareFile, Troy Hunt
You can skip to the end and leave a comment. Pinging is currently not allowed.
