Microsoft Uses Trademark Law to Disrupt Trickbot Botnet
![]()
Microsoft Corp. has executed a coordinated legal sneak attack in a bid to disrupt the malware-as-a-service botnet Trickbot, a global menace that has infected millions of computers and is used to spread ransomware. A court in Virginia granted Microsoft control over many Internet servers Trickbot uses to plunder infected systems, based on novel claims that the crime machine abused the software giant’s trademarks. However, it appears the operation has not completely disabled the botnet.
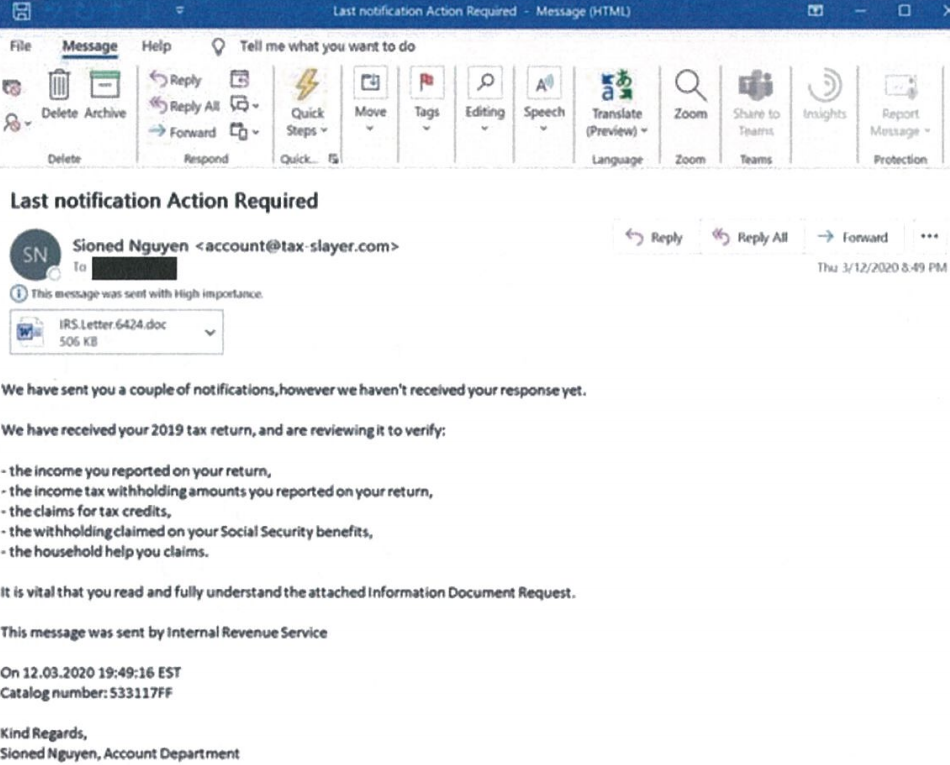
A spam email containing a Trickbot-infected attachment that was sent earlier this year. Image: Microsoft.
“We disrupted Trickbot through a court order we obtained as well as technical action we executed in partnership with telecommunications providers around the world,” wrote Tom Burt, corporate vice president of customer security and trust at Microsoft, in a blog post this morning about the legal maneuver. “We have now cut off key infrastructure so those operating Trickbot will no longer be able to initiate new infections or activate ransomware already dropped into computer systems.”
Microsoft’s action comes just days after the U.S. military’s Cyber Command carried out its own attack that sent all infected Trickbot systems a command telling them to disconnect themselves from the Internet servers the Trickbot overlords used to control them. The roughly 10-day operation by Cyber Command also stuffed millions of bogus records about new victims into the Trickbot database in a bid to confuse the botnet’s operators.
In legal filings, Microsoft argued that Trickbot irreparably harms the company “by damaging its reputation, brands, and customer goodwill. Defendants physically alter and corrupt Microsoft products such as the Microsoft Windows products. Once infected, altered and controlled by Trickbot, the Windows operating system ceases to operate normally and becomes tools for Defendants to conduct their theft.”
From the civil complaint Microsoft filed on October 6 with the U.S. District Court for the Eastern District of Virginia:
“However, they still bear the Microsoft and Windows trademarks. This is obviously meant to and does mislead Microsoft’s customers, and it causes extreme damage to Microsoft’s brands and trademarks.”
“Users subject to the negative effects of these malicious applications incorrectly believe that Microsoft and Windows are the source of their computing device problems. There is great risk that users may attribute this problem to Microsoft and associate these problems with Microsoft’s Windows products, thereby diluting and tarnishing the value of the Microsoft and Windows trademarks and brands.”
Microsoft said it will leverage the seized Trickbot servers to identify and assist Windows users impacted by the Trickbot malware in cleaning the malware off of their systems.
Trickbot has been used to steal passwords from millions of infected computers, and reportedly to hijack access to well more than 250 million email accounts from which new copies of the malware are sent to the victim’s contacts.
Trickbot’s malware-as-a-service feature has made it a reliable vehicle for deploying various strains of ransomware, locking up infected systems on a corporate network unless and until the company agrees to make an extortion payment.
A particularly destructive ransomware strain that is closely associated with Trickbot — known as “Ryuk” or “Conti” — has been responsible for costly attacks on countless organizations over the past year, including healthcare providers, medical research centers and hospitals.
One recent Ryuk victim is Universal Health Services (UHS), a Fortune 500 hospital and healthcare services provider that operates more than 400 facilities in the U.S. and U.K.
On Sunday, Sept. 27, UHS shut down its computer systems at healthcare facilities across the United States in a bid to stop the spread of the malware. The disruption caused some of the affected hospitals to redirect ambulances and relocate patients in need of surgery to other nearby hospitals.
Microsoft said it did not expect its action to permanently disrupt Trickbot, noting that the crooks behind the botnet will likely make efforts to revive their operations. But so far it’s not clear whether Microsoft succeeded in commandeering all of Trickbot’s control servers, or when exactly the coordinated seizure of those servers occurred.
As the company noted in its legal filings, the set of Internet address used as Trickbot controllers is dynamic, making attempts to disable the botnet more challenging.
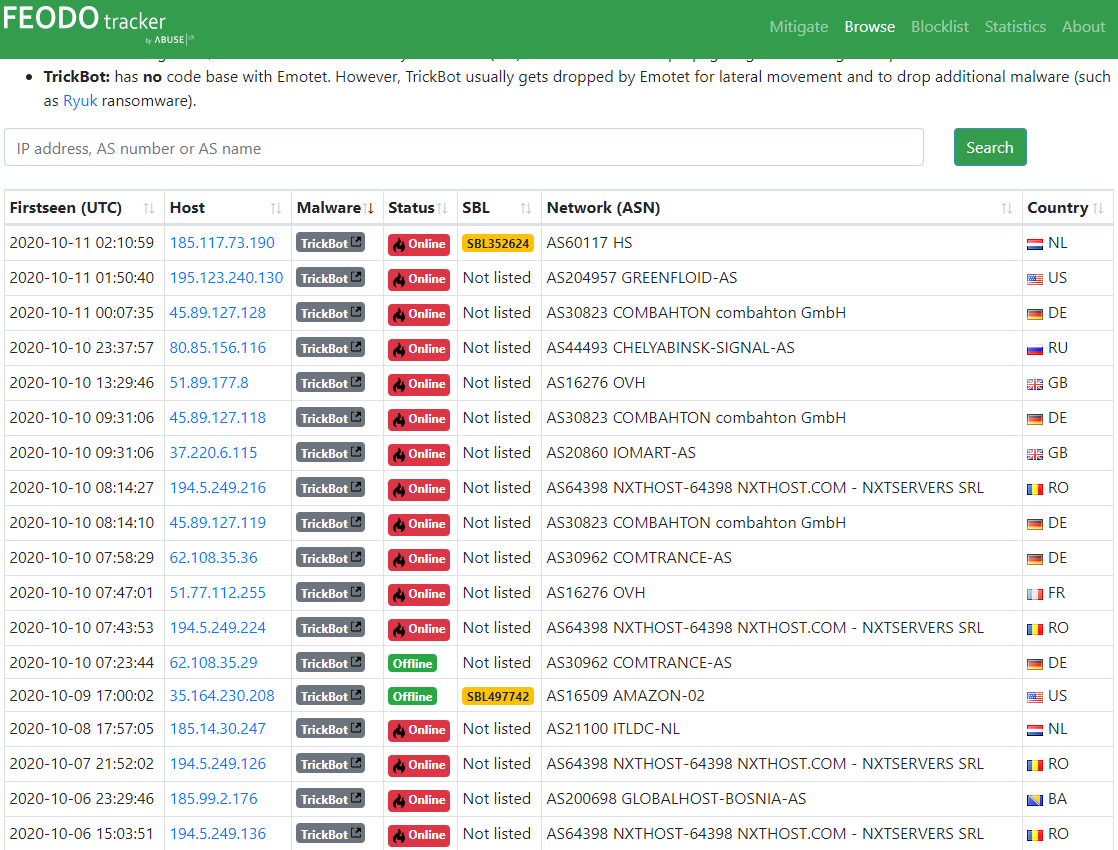
Indeed, according to real-time information posted by Feodo Tracker, a Swiss security site that tracks Internet servers used as controllers for Trickbot and other botnets, nearly two dozen Trickbot control servers — some of which first went active at beginning of this month — are still live and responding to requests at the time of this publication.
Cyber intelligence firm Intel 471 says fully taking down Trickbot would require an unprecedented level of collaboration among parties and countries that most likely would not cooperate anyway. That’s partly because Trickbot’s primary command and control mechanism supports communication over The Onion Router (TOR) — a distributed anonymity service that is wholly separate from the regular Internet.
“As a result, it is highly likely a takedown of the Trickbot infrastructure would have little medium- to long-term impact on the operation of Trickbot,” Intel 471 wrote in an analysis of Microsoft’s action.
What’s more, Trickbot has a fallback communications method that uses a decentralized domain name system called EmerDNS, which allows people to create and use domains that cannot be altered, revoked or suspended by any authority. The highly popular cybercrime store Joker’s Stash — which sells millions of stolen credit cards — also uses this setup.
From the Intel 471 report [malicious links and IP address defanged with brackets]:
“In the event all Trickbot infrastructure is taken down, the cybercriminals behind Trickbot will need to rebuild their servers and change their EmerDNS domain to point at their new servers. Compromised systems then should be able to connect to the new Trickbot infrastructure. Trickbot’s EmerDNS fall-back domain safetrust[.]bazar recently resolved to the IP address 195.123.237[.]156. Not coincidentally, this network neighborhood also hosts Bazar malware control servers.”
“Researchers previously attributed the development of the Bazar malware family to the same group behind Trickbot, due to code similarities with the Anchor malware family and its methods of operation, such as shared infrastructure between Anchor and Bazar. On Oct. 12, 2020 the fall-back domain resolved to the IP address 23.92.93[.]233, which was confirmed by Intel 471 Malware Intelligence systems to be a Trickbot controller URL in May 2019. This suggests the fall-back domain is still controlled by the Trickbot operators at the time of this report.”
Intel 471 concluded that the Microsoft action has so far has done little to disrupt the botnet’s activity.
“At the time of this report, Intel 471 has not seen any significant impact on Trickbot’s infrastructure and ability to communicate with Trickbot-infected systems,” the company wrote.
The legal filings from Microsoft are available here.
Update, 9:51 a.m. ET: Feodo Tracker now lists just six Trickbot controllers as responding. All six were first seen online in the past 48 hours. Also added perspective from Intel 471.
You can skip to the end and leave a comment. Pinging is currently not allowed.
Courtesy of: krebsonsecurity.com