Bug Bounty Hunter Ran ISP Doxing Service
![]()
A Connecticut man who’s earned bug bounty rewards and public recognition from top telecom companies for finding and reporting security holes in their Web sites secretly operated a service that leveraged these same flaws to sell their customers’ personal data, KrebsOnSecurity has learned.
In May 2018, ZDNet ran a story about the discovery of a glaring vulnerability in the Web site for wireless provider T-Mobile that let anyone look up customer home addresses and account PINs. The story noted that T-Mobile disabled the feature in early April after being alerted by a 22-year-old “security researcher” named Ryan Stevenson, and that the mobile giant had awarded Stevenson $1,000 for reporting the discovery under its bug bounty program.
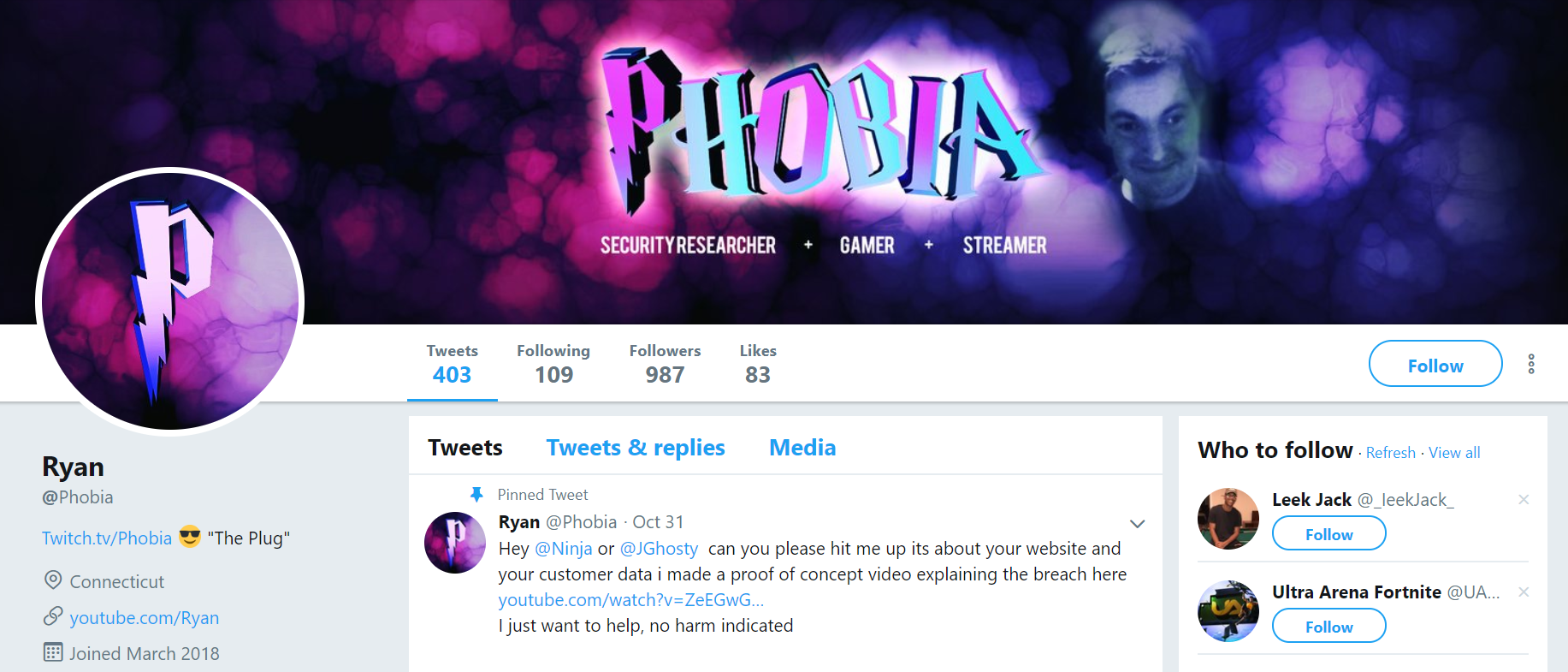
The Twitter account @phobia, a.k.a. Ryan Stevenson. The term “plug” referenced next to his Twitch profile name is hacker slang for employees at mobile phone stores who can be tricked or bribed into helping with SIM swap attacks.
Likewise, AT&T has recognized Stevenson for reporting security holes in its services. AT&T’s bug bounty site lets contributors share a social media account or Web address where they can be contacted, and in Stevenson’s case he gave the now-defunct Twitter handle “@Phoobia.”
Stevenson’s Linkedin profile — named “Phobias” — says he specializes in finding exploits in numerous Web sites, including hotmail.com, yahoo.com, aol.com, paypal.com and ebay.com. Under the “contact info” tab of Stevenson’s profile it lists the youtube.com account of “Ryan” and the Facebook account “Phobia” (also now deleted).
Coincidentally, I came across multiple variations on this Phobia nickname as I was researching a story published this week on the epidemic of fraudulent SIM swaps, a complex form of mobile phone fraud that is being used to steal millions of dollars in cryptocurrencies.
Unauthorized SIM swaps also are often used to hijack so-called “OG” user accounts — usually short usernames on top social network and gaming Web sites that are highly prized by many hackers because they can make the account holder appear to have been a savvy, early adopter of the service before it became popular and before all of the short usernames were taken. Some OG usernames can be sold for thousands of dollars in underground markets.
This week’s SIM swapping story quoted one recent victim who lost $100,000 after his mobile phone number was briefly stolen in a fraudulent SIM swap. The victim said he was told by investigators in Santa Clara, Calif. that the perpetrators of his attack were able to access his T-Mobile account information using a specialized piece of software that gave them backdoor access to T-Mobile’s customer database.
Both the Santa Clara investigators and T-Mobile declined to confirm or deny the existence of this software. But their non-denials prompted me to start looking for it on my own. So naturally I began searching at ogusers-dot-com, a forum dedicated to the hacking, trading and sale of OG accounts. Unsurprisingly, ogusers-dot-com also has traditionally been the main stomping grounds for many individuals involved in SIM swapping attacks.
It didn’t take long to discover an account on ogusers named “Ryan,” who for much of 2018 has advertised a number of different “doxing” services — specifically those aimed at finding the personal information of customers at major broadband and telecom companies.
In some of Ryan’s sales threads, fellow forum members refer to him as “Phob” or “Phobs.” In a post on May 27, Ryan says he’s willing to pay or trade for OG accounts under the name “Ryan,” “Ryans”, “RS,” “RMS” or “Stevenson” on any decent sized popular Web site. “hmu [hit me up] in a pm [private message] to talk,” Ryan urged fellow forum members.
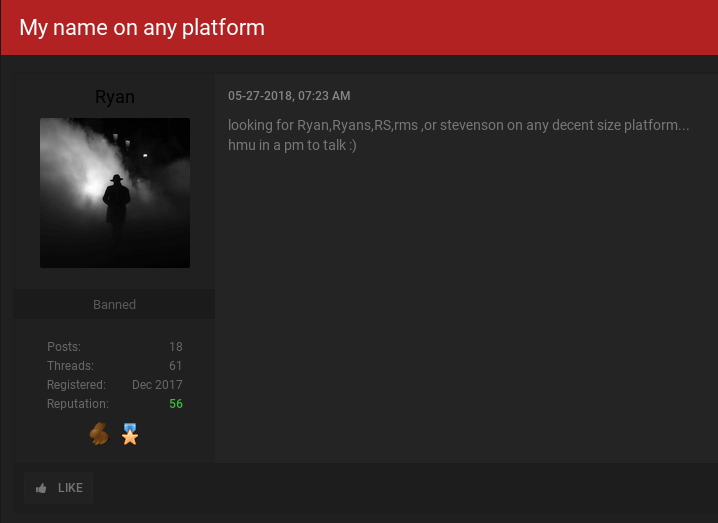
The OG User forum account “Ryan” asking fellow members to sell or trade him any major Web site account name that includes the OG username “Ryan” or “Stevenson.”
I found that as late as June 2018 Ryan was offering a service that he claimed was capable of “doxing any usa carrier,” including Verizon, AT&T, Sprint, T-Mobile, MetroPCS and Boost Mobile.
“All I need is the number,” Ryan said of his customer data lookup service, which he sold for $25 per record. “Payment BTC [bitcoin] only.”
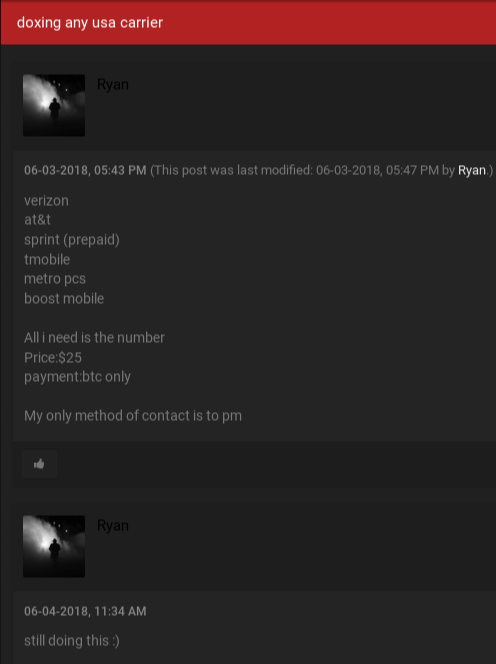
For $25 per record, Ryan offered fellow ogusers members the ability to look up customer records tied to any customer of the major U.S. mobile providers.
Very similar offerings were made by Phobia’s alter ego “AOLer” on the sprawling English language online hacking community Hackforums.
I first encountered Stevenson several years back while trying to work out who was responsible for calling in a phony hostage situation and sending a heavily armed police force to our Northern Virginia home in 2013. In a follow-up to that story, Stevenson admitted that he was responsible for the high-profile hack against Wired reporter Mat Honan, who documented how a hacker named Phobia had deleted his Google account and remotely erased all data from his iPhone, iPad and MacBook.
Going by the nickname “Phobiathegod” at the time, Stevenson was then part of a group of young men who routinely hijacked OG account names on Microsoft’s Xbox gaming platform, often using methods that involved tricking customer service people at the target’s mobile provider into transferring the victim’s calls to a number they controlled.
Fast forward to today, and Phobia’s main Twitter account (pictured at the top of this post) includes the phrase “the plug” next to his profile. In SIM swapping circles, a “plug” is hacker slang for an employee at a mobile phone store who can be bribed, tricked or blackmailed into assisting with an unauthorized SIM swap.
Reached via instant message on LinkedIn, Stevenson acknowledged running the ISP doxing services, but said his account on the OGusers forum was since banned and that hardly anyone took him up on his offer anyway.
“I shouldn’t have made the threads even though no one really asked for anything,” he said. “I’m on the good side. But its almost 2019 and I need to find a new hobby I can’t be bothered to look for breaches/vulns, haven’t got 1 job offer or recommendation yet.”
Asked about “the plug” reference in his Twitter profile, Stevenson suddenly stopped replying. Not long after that, the @Phobia Twitter account was deactivated.
Stevenson denied being involved in SIM swapping attacks, but it is clear Phobia was fairly tight with many people who are or until recently were at the center of this scene. In July 2018, authorities in California arrested 20-year-old Boston resident Joel Ortiz for allegedly conducting dozens of fraudulent SIM swaps and stealing at least $5 million worth of cryptocurrency from victims.
Like Phobia, Ortiz had a presence on OGusers and had acquired some of the most OG social media accounts available, including the Twitter and Instagram account names with the number zero (@0), and the OG Youtube accounts “Joel” and “X”.
On Oct 27, 2017, the Youtube account “Joel” published a 4-minute video of Stevenson dancing to a popular rap song in front of the camera. On July 5, 2018, just days before Ortiz was arrested, the Twitter account “0” gave a shout out to @Phobia on Twitter suggesting Phobia was actually tweeting using Ortiz’s “0” account.
Tags: aoler, Hackforums, Joel Ortiz, Mat Honan, Microsoft Xbox, OG, ogusers, Phobia, Phobias, Ryan, Ryan Stevenson, SIM swap, T-Mobile, wired
You can skip to the end and leave a comment. Pinging is currently not allowed.